Cryptobox
What is Cryptobox?
Cryptobox is a simple javascript-based encryption application designed to illustrate the principles of cryptography. The algorithm used by Cryptobox is based loosely on DES, a cipher developed by IBM and the NSA in the '70s. Due to advances in cryptanalysis and computing, DES is no longer secure, but it provides an interesting study of the methods used to hide data in plain sight.Cryptobox's cipher uses a 16-bit key to transform blocks of 16 bits at a time. To provide better security for long messages, the cipher uses the CBC mode of operation to encrypt the message.
DISCLAIMER: Cryptobox is in no way a secure system. It is designed to allow experimentation with cryptography, and should not be used to protect sensitive data.
Using Cryptobox
Enter the text you would like to encrypt in the left text box. Enter a key, which should be four hex digits, or click "Random" to have a random key selected for you. Click "Encrypt" to produce encrypted output in the right panel.To decrypt encrypted text, enter the ciphertext in the right panel, enter the key, and click "Decrypt." The decrypted text will appear in the left panel. If you don't know the key, click "Crack," and Cryptobox will brute-force the decryption, trying each key on the ciphertext. The Key field will show the progress, and the key if it is found. Note that if the ciphertext is damaged, decryption will be impossible.
To save the ciphertext for later retrieval, click "Save Encrypted." The ciphertext will be saved on the server, and you will be redirected to a URL that uniquely describes that ciphertext. You can then bookmark the URL, send it to a friend, or do anything else you can do with a URL.
Technical Discussion
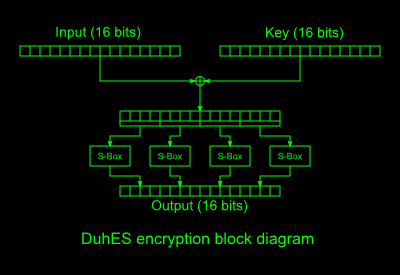
DuhES
Cryptobox's cipher is a beast of my own invention called DuhES. The implementation resides in cryptobox.js. The core block cipher of DuhES operates on 16 bits of plaintext and a 16-bit key. The key and plaintext are XORed together, then run through a permutation function that runs each nybble through a S-box. This is repeated 16 times. Decryption is the reverse: The block is run through a reverse permutation function which transforms each nybble through a reverse S-box, then the result is XORed with the key, repeated 16 times.S-boxes
An S-box, short for "Substitution Box," is a non-linear transformation that turns one number into another, typically via bit manipulation or a lookup table. DuhES uses a S-box generated from digits of π with a simple perl script:
#!/usr/bin/perl
# Generate S-boxes from pi
use strict;
my (@sbox, @rsbox);
# Digits of PI from http://www.joyofpi.com/pi.html
my @PI = (1415926535,8979323846,2643383279,5028841971,6939937510);
my $PI = pop @PI;
for (0..15) {
# Select four bits
my $b;
do {
$b = $PI & 0xF;
$PI >>= 4;
$PI = pop @PI if $PI == 0;
} while (exists $rsbox[$b]);
$sbox[$_] = $b;
$rsbox[$b] = $_;
}
print 'var sbox = [', join(',', @sbox), "];\n";
print 'var rsbox = [', join(',', @rsbox), "];\n";
The use of known constants in cryptographic functions is called a "Nothing up my sleeve number," which is used to put at ease any fears that the S-boxes were engineered to have weaknesses that I could exploit. This does not mean that they don't have weaknesses, mind you, just that I didn't intend any. Running the script gives us our S-boxes:
var sbox = [6,14,10,0,7,13,9,1,3,15,11,2,8,12,5,4]; var rsbox = [3,7,11,8,15,14,0,4,12,6,2,10,13,5,1,9];
Rsbox is the reverse of the S-box, used during decryption to reverse the process. To transform a number, it is "looked up" in the sbox array, and the number in that position is substituted. For example, the S-box transformation of 7 is 1. Remember that arrays count from zero.
CBC mode
By itself, a block cipher can safely obscure one block. Used many times to encrypt a long message, patterns will occur due to repeated input blocks producing repeated output blocks. The result can be analyzed much like the Caesar cipher puzzles in the newspaper. To more effectively obscure messages longer than the block size (in our case, 16 bits), we use a mode of operation to transform the message as we go.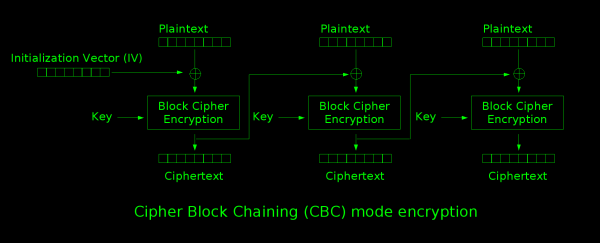 DuhES uses
the CBC mode of operation, which uses an Initialization Vector
(abbreviated IV) in addition to the key. At the beginning of the
encryption process, the IV is XORed with a block's worth of plaintext,
and run through the encryption. This result becomes the IV for the next
round, and the process is repeated until no more plaintext remains.
DuhES uses
the CBC mode of operation, which uses an Initialization Vector
(abbreviated IV) in addition to the key. At the beginning of the
encryption process, the IV is XORed with a block's worth of plaintext,
and run through the encryption. This result becomes the IV for the next
round, and the process is repeated until no more plaintext remains.
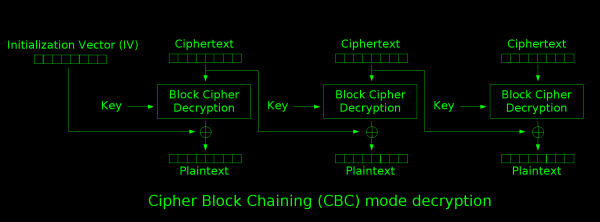 Decryption flips the process on its head, first
decrypting a block of ciphertext, then XORing the result with the IV to
produce the first block of plaintext. The first block of ciphertext is
then used as the IV for the next stage, and so on.
Decryption flips the process on its head, first
decrypting a block of ciphertext, then XORing the result with the IV to
produce the first block of plaintext. The first block of ciphertext is
then used as the IV for the next stage, and so on.
There is a problem, however, with this approach. Since a block cipher can only encrypt or decrypt a block at a time, if the message is not long enough to fill an entire block at the end, the message must be padded to fill a whole block. DuhES pads the final block with null bytes if necessary (which, since the block size is only 16 bits, will add at most one byte). On decryption, null bytes are removed from the output. This has a side effect of making the encryption/decryption process not suitable for binary data, but since all we're doing is encrypting text, it's not a concern.
Ciphertext Format
You may have noticed, when playing with Cryptobox, that the ciphertext output is significantly larger than the input. The output contains the encrypted bytes in a hex string format, expanding the output to two characters per byte and ensuring that it can be copied and pasted without corruption. Furthermore, the first 16 bytes of the ciphertext are a MD5 hash of the plaintext used to verify proper decryption. The last four bytes of this hash are also used as the IV for CBC output.Questions To Ponder
- Why is the size of the key important in a cipher?
- Why is XOR used instead of OR or AND?
- Some elements of DES were not used in DuhES. How do these elements make DES more secure than DuhES?
- Why are S-boxes important?
- Is deriving the IV from the MD5 a bad idea?
- When using CBC mode, what happens to the output when one block of the ciphertext input is damaged?
- Would repeating the base DuhES encryption block more than 16 times provide additional security? Would repeating it less than 16 times provide less security?
- How does the use of encryption by civilians threaten government?
Things To Do If You're Bored
- Extend DuhES to work with 32-bit keys. If you're feeling especially ambitious, extend it to use 256-bit keys.
- Instead of using hex string output, change the encoder to output in something more compact like Base64.
- MD5 can only determine if the whole message is correct or not. Design an integrity checking system that allows partial recovery of damaged messages.